18. 设置社交身份认证¶
身份验证方法可简化最终用户的登录过程,使用现有登录信息提供单点登录以登录到第三方网站,而不是为该网站专门创建新登录帐户。
帐户身份验证可以在 automation controller 用户界面中配置并保存到 PostgreSQL 数据库。如需了解具体步骤,请参阅 Controller 配置 部分。
automation controller 中的帐户身份验证可以被配置为集中使用 OAuth2,企业级帐户身份验证可以配置 SAML、RADIUS 或 LDAP 作为身份验证信息来源。
对于提供帐户信息的网站,如 Microsoft Azure、Google 或 GitHub,则通常使用 OAuth 标准来实施帐户信息。OAuth 是一个安全授权协议,通常与帐户身份验证一同使用,以授予第 3 个方应用“会话令牌”,允许它们代表用户向提供程序发出 API 调用。
SAML(Security Assertion Markup Language)是一个基于 XML 的、开放式的数据格式,用于在身份提供程序和服务提供程序之间交换帐户身份验证和授权数据。
使用 RADIUS 分布式客户端/服务器系统,您可以保护网络不受未授权访问的影响,并可在为远程用户维护网络访问时需要高安全性的网络环境中实施。
18.1. GitHub 设置¶
To set up social authentication for GitHub, you will need to obtain an OAuth2 key and secret for a web application. To do this, you must first register the new application with GitHub at https://github.com/settings/developers. In order to register the application, you must supply it with your homepage URL, which is the Callback URL shown in the Details tab for the GitHub default settings page. The OAuth2 key (Client ID) and secret (Client Secret) will be used to supply the required fields in the automation controller User Interface.
点左侧导航栏中的 Settings。
在 Settings 窗口左侧,点 Authentication 选项列表中的 GitHub settings。
如果还没有选择,点 GitHub Default 标签页。
GitHub OAuth2 Callback URL 字段已预先填充且不可编辑。在应用程序被注册后,GitHub 会显示客户端 ID 和客户端 Secret。
点 Edit,将 GitHub 的客户端 ID 复制到 GitHub OAuth2 Key 字段中。
将 GitHub 的客户端 Secret 复制到 GitHub OAuth2 Secret 字段中。
如需完成映射字段的详情,请参阅 机构和团队映射。
完成后请点击 Save。
要验证是否已正确配置了身份验证,请注销 automation controller,登录屏幕现在将会显示 GitHub 徽标,以允许使用这些凭证登录。
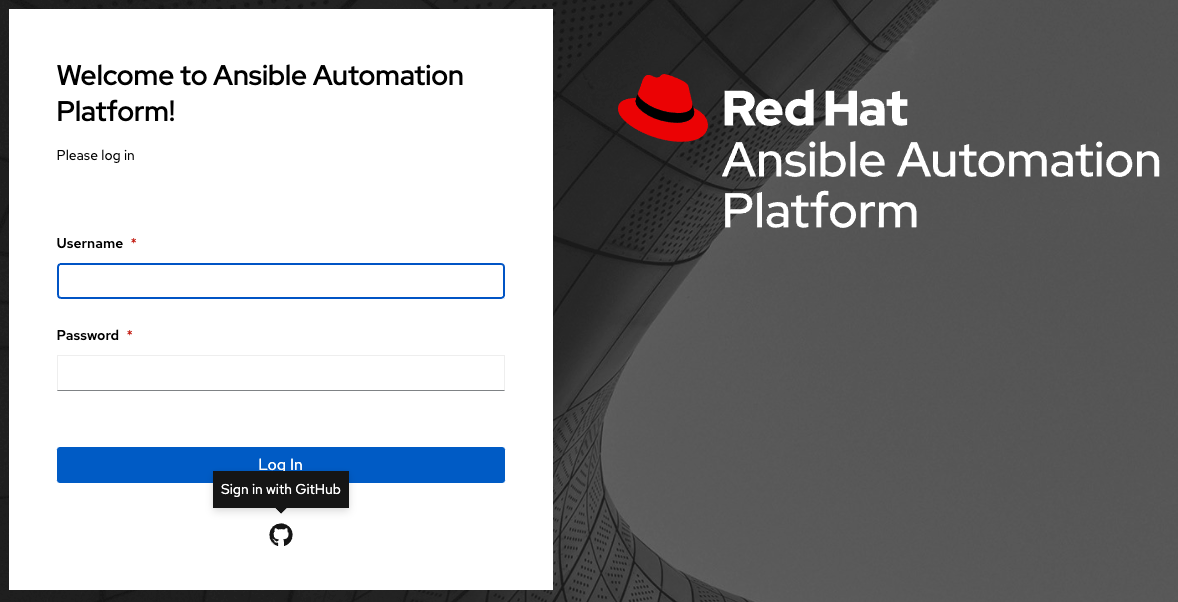
18.1.1. GitHub Organization settings¶
当使用机构或者机构中团队定义帐户身份验证时,您应该使用特定的机构和团队设置。帐户身份验证可以受机构以及机构中团队的限制。
您还可以通过指定基于非机构或非团队的设置(如上所示)来选择允许所有设置。
您可以限制只有某个机构或者机构中的某个团队的用户才可以登陆到控制器。
To set up social authentication for a GitHub Organization, you will need to obtain an OAuth2 key and secret for a web application. To do this, you must first register your organization-owned application at https://github.com/organizations/<yourorg>/settings/applications. In order to register the application, you must supply it with your Authorization callback URL, which is the Callback URL shown in the Details page. Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) will be used to supply the required fields in the automation controller User Interface.
点左侧导航栏中的 Settings。
在 Settings 窗口左侧,点 Authentication 选项列表中的 GitHub settings。
点 GitHub Organization 标签页。
GitHub Organization OAuth2 Callback URL 字段已预先填充且不可编辑。
注册应用程序后,GitHub 会显示客户端 ID 和客户端 Secret。
点 Edit,将 GitHub 的客户端 ID 复制到 GitHub Organization OAuth2 Key 字段中。
将 GitHub 的客户端 Secret 复制并粘贴到 GitHub Organization OAuth2 Secret 字段中。
Enter the name of your GitHub organization, as used in your organization's URL (e.g., https://github.com/<yourorg>/) in the GitHub Organization Name field.
如需完成映射字段的详情,请参阅 机构和团队映射。
完成后请点击 Save。
要验证是否已正确配置了身份验证,请先退出 automation controller。登录屏幕现在将会显示 GitHub 机构徽标来允许使用这些凭证登陆到 automation controller。

18.1.2. GitHub 团队设置¶
To set up social authentication for a GitHub Team, you will need to obtain an OAuth2 key and secret for a web application. To do this, you must first register your team-owned application at https://github.com/organizations/<yourorg>/settings/applications. In order to register the application, you must supply it with your Authorization callback URL, which is the Callback URL shown in the Details page. Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) will be used to supply the required fields in the automation controller User Interface.
使用 GitHub API 查找团队 ID:http://fabian-kostadinov.github.io/2015/01/16/how-to-find-a-github-team-id/。团队 ID 将用于提供 automation controller 用户界面中所需的字段。
点左侧导航栏中的 Settings。
在 Settings 窗口左侧,点 Authentication 选项列表中的 GitHub settings。
点 GitHub Team 标签页。
GitHub Team OAuth2 Callback URL 字段已预先填充且不可编辑。在应用程序被注册后,GitHub 会显示客户端 ID 和客户端 Secret。
点 Edit,将 GitHub 的客户端 ID 复制到 GitHub Team OAuth2 Key 字段中。
将 GitHub 的客户端 Secret 复制并粘贴到 GitHub Team OAuth2 Secret 字段中。
Copy and paste GitHub's team ID in the GitHub Team ID field.
如需完成映射字段的详情,请参阅 机构和团队映射。
完成后请点击 Save。
要验证是否已正确配置了身份验证,请注销 automation controller,登录屏幕现在将会显示 GitHub 团队徽标,以允许使用这些凭证登录。
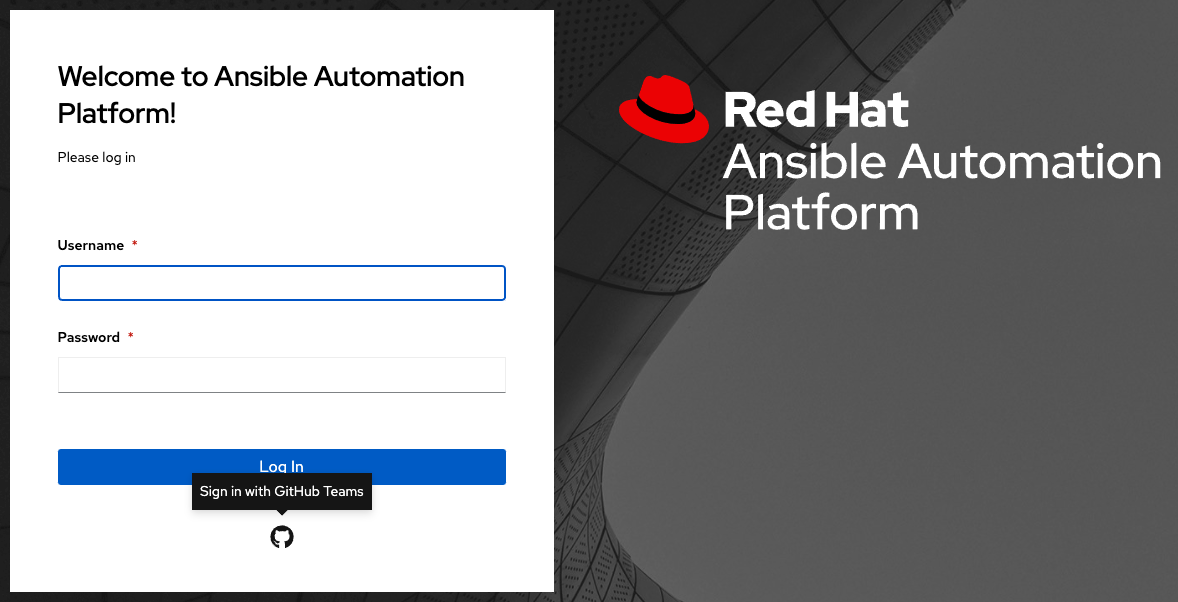
18.1.3. GitHub Enterprise settings¶
To set up social authentication for a GitHub Enterprise, you will need to obtain a GitHub Enterprise URL, an API URL, OAuth2 key and secret for a web application. To obtain the URLs, refer to the GitHub documentation on GitHub Enterprise administration . To obtain the key and secret, you must first register your enterprise-owned application at https://github.com/organizations/<yourorg>/settings/applications. In order to register the application, you must supply it with your Authorization callback URL, which is the Callback URL shown in the Details page. Because its hosted on site and not github.com, you must specify which auth adapter it will talk to.
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) will be used to supply the required fields in the automation controller User Interface.
点左侧导航栏中的 Settings。
在 Settings 窗口左侧,点 Authentication 选项列表中的 GitHub settings。
Click the GitHub Enterprise tab.
The GitHub Enterprise OAuth2 Callback URL field is already pre-populated and non-editable. Once the application is registered, GitHub displays the Client ID and Client Secret.
Click Edit to configure GitHub Enterprise settings.
In the GitHub Enterprise URL field, enter the hostname of the GitHub Enterprise instance (e.g., https://github.example.com).
In the GitHub Enterprise API URL field, enter the API URL of the GitHub Enterprise instance (e.g., https://github.example.com/api/v3)
Copy and paste GitHub's Client ID into the GitHub Enterprise OAuth2 Key field.
Copy and paste GitHub's Client Secret into the GitHub Enterprise OAuth2 Secret field.
如需完成映射字段的详情,请参阅 机构和团队映射。
完成后请点击 Save。
To verify that the authentication was configured correctly, logout of automation controller and the login screen will now display the GitHub Enterprise logo to allow logging in with those credentials.
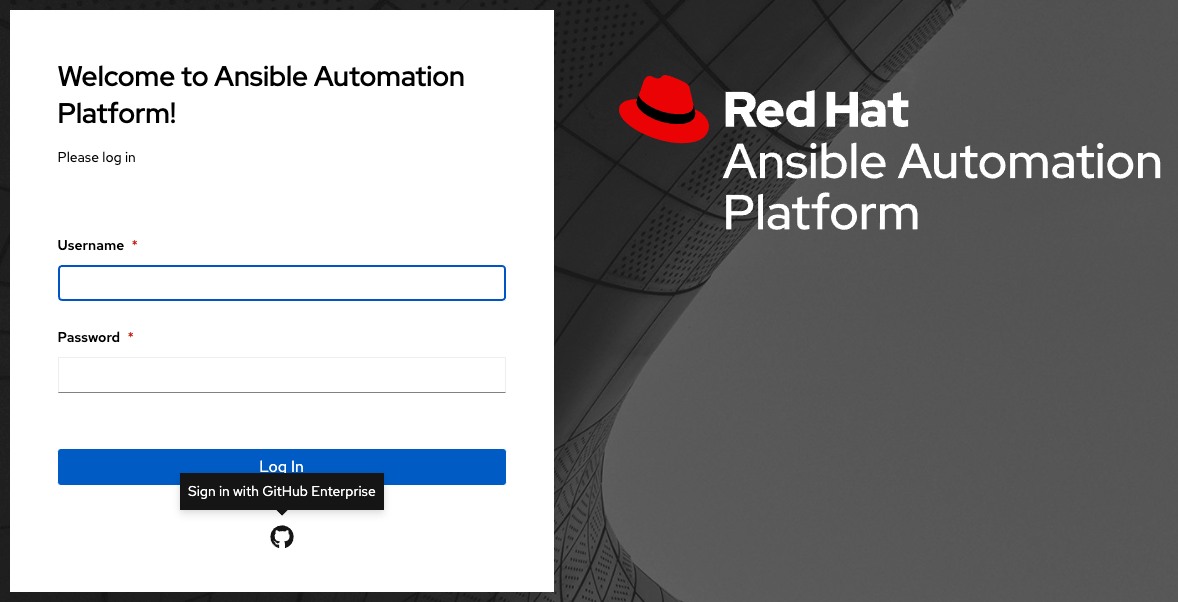
18.1.4. GitHub Enterprise Organization settings¶
To set up social authentication for a GitHub Enterprise Org, you will need to obtain a GitHub Enterprise Org URL, an Org API URL, an Org OAuth2 key and secret for a web application. To obtain the URLs, refer to the GitHub documentation on GitHub Enterprise administration . To obtain the key and secret, you must first register your enterprise organization-owned application at https://github.com/organizations/<yourorg>/settings/applications. In order to register the application, you must supply it with your Authorization callback URL, which is the Callback URL shown in the Details page. Because its hosted on site and not github.com, you must specify which auth adapter it will talk to.
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) will be used to supply the required fields in the automation controller User Interface.
点左侧导航栏中的 Settings。
在 Settings 窗口左侧,点 Authentication 选项列表中的 GitHub settings。
Click the GitHub Enterprise Organization tab.
The GitHub Enterprise Organization OAuth2 Callback URL field is already pre-populated and non-editable. Once the application is registered, GitHub displays the Client ID and Client Secret.
Click Edit to configure GitHub Enterprise Organization settings.
In the GitHub Enterprise Organization URL field, enter the hostname of the GitHub Enterprise Org instance (e.g., https://github.orgexample.com).
In the GitHub Enterprise Organization API URL field, enter the API URL of the GitHub Enterprise Org instance (e.g., https://github.orgexample.com/api/v3)
Copy and paste GitHub's Client ID into the GitHub Enterprise Organization OAuth2 Key field.
Copy and paste GitHub's Client Secret into the GitHub Enterprise Organization OAuth2 Secret field.
Enter the name of your GitHub Enterprise organization, as used in your organization's URL (e.g., https://github.com/<yourorg>/) in the GitHub Enterprise Organization Name field.
如需完成映射字段的详情,请参阅 机构和团队映射。
完成后请点击 Save。
To verify that the authentication was configured correctly, logout of automation controller and the login screen will now display the GitHub Enterprise Organization logo to allow logging in with those credentials.

18.1.5. GitHub Enterprise Team settings¶
To set up social authentication for a GitHub Enterprise teams, you will need to obtain a GitHub Enterprise Org URL, an Org API URL, an Org OAuth2 key and secret for a web application. To obtain the URLs, refer to the GitHub documentation on GitHub Enterprise administration . To obtain the key and secret, you must first register your enterprise team-owned application at https://github.com/organizations/<yourorg>/settings/applications. In order to register the application, you must supply it with your Authorization callback URL, which is the Callback URL shown in the Details page. Because its hosted on site and not github.com, you must specify which auth adapter it will talk to.
Each key and secret must belong to a unique application and cannot be shared or reused between different authentication backends. The OAuth2 key (Client ID) and secret (Client Secret) will be used to supply the required fields in the automation controller User Interface.
使用 GitHub API 查找团队 ID:http://fabian-kostadinov.github.io/2015/01/16/how-to-find-a-github-team-id/。团队 ID 将用于提供 automation controller 用户界面中所需的字段。
点左侧导航栏中的 Settings。
在 Settings 窗口左侧,点 Authentication 选项列表中的 GitHub settings。
Click the GitHub Enterprise Team tab.
The GitHub Enterprise Team OAuth2 Callback URL field is already pre-populated and non-editable. Once the application is registered, GitHub displays the Client ID and Client Secret.
Click Edit to configure GitHub Enterprise Team settings.
In the GitHub Enterprise Team URL field, enter the hostname of the GitHub Enterprise team instance (e.g., https://github.teamexample.com).
In the GitHub Enterprise Team API URL field, enter the API URL of the GitHub Enterprise team instance (e.g., https://github.teamexample.com/api/v3)
Copy and paste GitHub's Client ID into the GitHub Enterprise Team OAuth2 Key field.
Copy and paste GitHub's Client Secret into the GitHub Enterprise Team OAuth2 Secret field.
Copy and paste GitHub's team ID in the GitHub Enterprise Team ID field.
如需完成映射字段的详情,请参阅 机构和团队映射。
完成后请点击 Save。
To verify that the authentication was configured correctly, logout of automation controller and the login screen will now display the GitHub Enterprise Teams logo to allow logging in with those credentials.
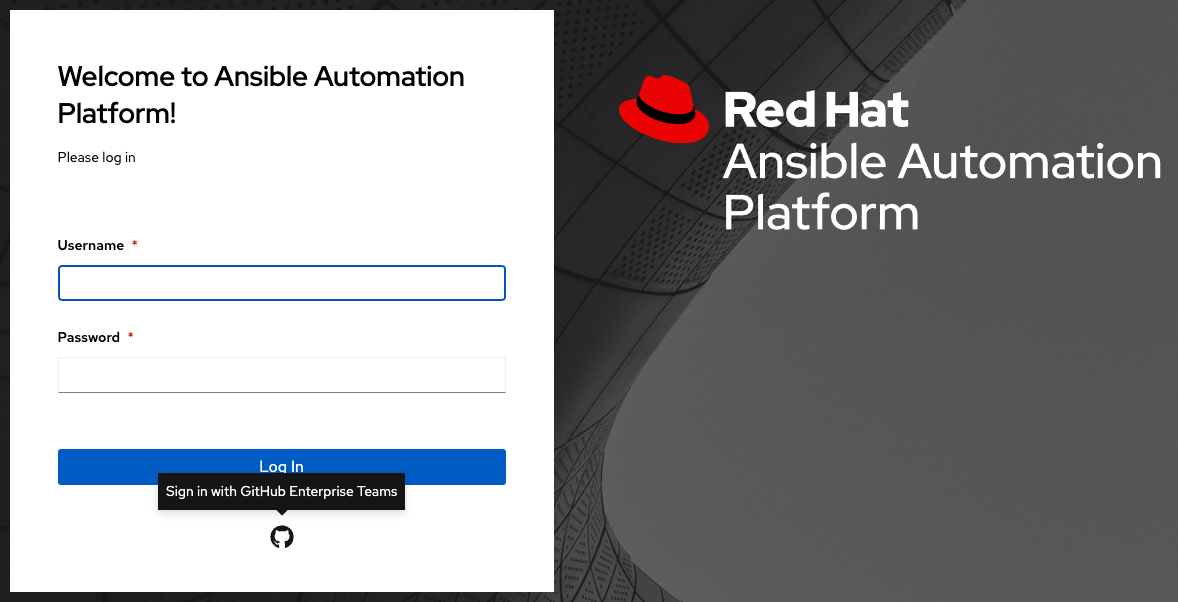
18.2. Google OAuth2 设置¶
要设置 Google 的身份验证,您需要获取 web 应用程序的 OAuth2 密钥和 secret。为此,您必须首先创建一个项目并使用 Google 进行设置。如需相关说明,请参阅 https://support.google.com/googleapi/answer/6158849。如果您已经完成了设置过程,您可以进入该 Google API Manager Console 的 Credentials 部分来访问这些凭证。OAuth2 密钥(客户端 ID)和 secret(客户端 secret)将用于提供 automation controller 用户界面中所需的字段。
点左侧导航栏中的 Settings。
在 Settings 窗口左侧,点 Authentication 选项列表中的 Google OAuth 2 settings。
Google OAuth2 Callback URL 字段已预先填充且不可编辑。
以下字段也会预先填充。如果没有,请使用 web 应用设置过程中提供的 Google 凭证,并寻找与以下示例中所示相同格式的值:
点 Edit,将 Google 的客户端 ID 复制到 Google OAuth2 Key 字段中。
将 Google 的客户端 secret 复制并粘贴到 Google OAuth2 Secret 字段中。
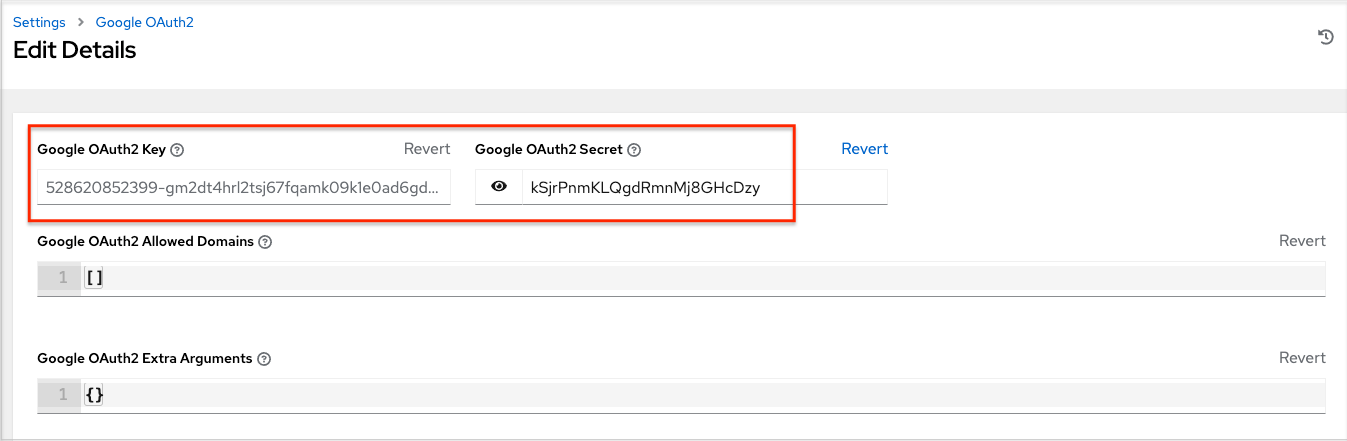
要完成剩余的可选字段,请参考每个字段中的工具提示,以获得说明和所需格式。
如需完成映射字段的详情,请参阅 机构和团队映射。
完成后请点击 Save。
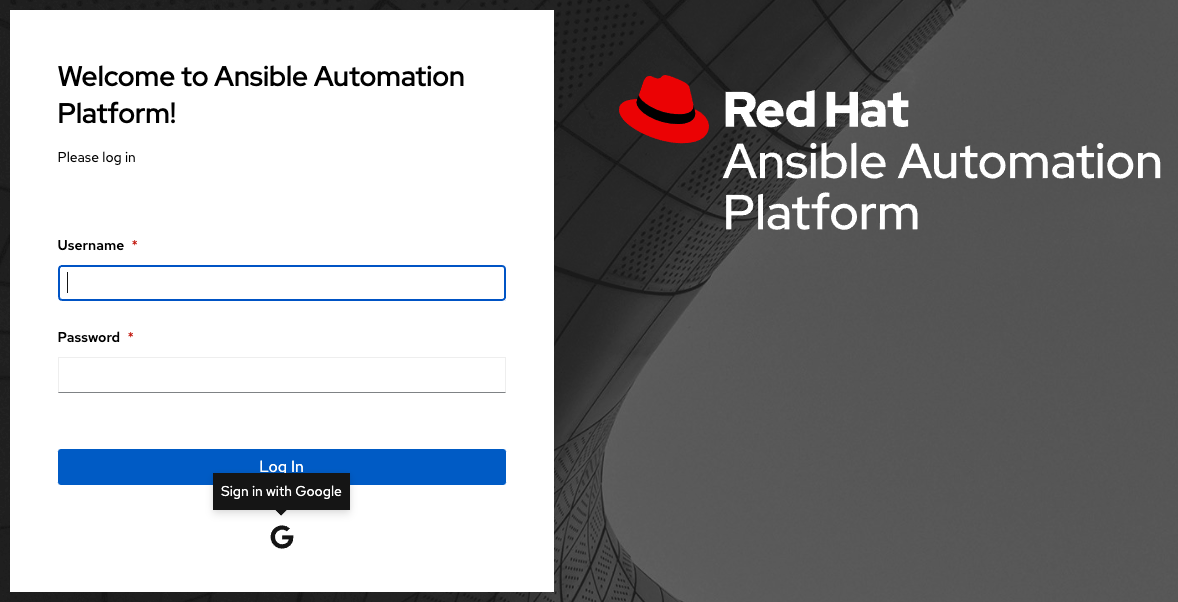
要验证是否已正确配置了身份验证,请注销 automation controller,登录屏幕现在将会显示 Google 徽标,以指定它作为登录 automation controller 的替代方法。
18.3. 机构和团队映射¶
18.3.1. 机构映射¶
您将需要根据用户名和电子邮件地址控制哪些用户放置到哪个控制器机构(从社交或企业身份验证帐户映射您的机构管理员/用户)。
字典键是机构名称。如果不存在机构以及许可证允许多个机构,则将创建机构。否则,无论键是什么均使用单一默认机构。
值是字典,用于定义每个机构成员资格的选项。对于每个机构来说,可以指定哪个用户自动成为机构的用户,以及哪个用户可以管理机构。
admins:None、True/False、字符串或字符串的列表/元组。
如果为 None,机构管理员将不会更新。
如果为 True,使用帐户身份验证的所有用户将自动添加为机构管理员。
如果为 False,则没有帐户身份验证用户自动添加为机构的管理员。
如果为字符串或字符串列表,指定要添加到机构中的用户的用户名和电子邮件。以
/开头和结尾的字符串将编译成正则表达式;修饰符i(区分大小写)和m``(多行)可在结束 ``/后指定。
remove_admins:True/False。默认为 True。
当为 True 时,不匹配的用户将从机构的管理列表中删除。
users:None、True/False、字符串或字符串列表/元组。应用的规则与 admins 相同。
remove_users:True/False。默认为 True。应用的规则与 remove_admins 相同。
{
"Default": {
"users": true
},
"Test Org": {
"admins": ["[email protected]"],
"users": true
},
"Test Org 2": {
"admins": ["[email protected]", "/^controller-[^@]+?@.*$/i"],
"users": "/^[^@].*?@example\\.com$/"
}
}
可以为每个帐户身份验证后端单独指定机构映射。如果已定义,这些配置将优先于上述全局配置。
SOCIAL_AUTH_GOOGLE_OAUTH2_ORGANIZATION_MAP = {}
SOCIAL_AUTH_GITHUB_ORGANIZATION_MAP = {}
SOCIAL_AUTH_GITHUB_ORG_ORGANIZATION_MAP = {}
SOCIAL_AUTH_GITHUB_TEAM_ORGANIZATION_MAP = {}
SOCIAL_AUTH_SAML_ORGANIZATION_MAP = {}
18.3.2. 团队映射¶
团队映射是从社交身份验证帐户的团队成员(用户)的映射。键是团队名称(如果不存在就会创建)。值是每个团队成员资格选项的字典,其中每项可以包含以下参数:
organization:字符串。团队所属机构的名称。如果机构和团队名称的组合不存在,则会创建团队。如果该机构不存在,则会首先创建机构。如果许可证不允许多个机构,团队将始终被分配给单一的默认机构。
users:None、True/False、字符串或字符串列表/元组。
如果为 None,则不会更新团队成员。
如果为 True/False,则所有社交身份验证用户将作为团队成员添加/删除。
如果为字符串或字符串列表,指定用于匹配用户的表达式。如果用户名或电子邮件匹配,用户将被添加为团队成员。以
/开头和结尾的字符串将编译成正则表达式;修饰符i``(区分大小)和 ``m``(多行)可以在 ``/结束后指定。
remove:True/False。默认为 True。当 True 时,与规则不匹配的用户将从团队中删除。
{
"My Team": {
"organization": "Test Org",
"users": ["/^[^@]+?@test\\.example\\.com$/"],
"remove": true
},
"Other Team": {
"organization": "Test Org 2",
"users": ["/^[^@]+?@test\\.example\\.com$/"],
"remove": false
}
}
可以根据您的设置,为每个帐户身份验证后端单独指定团队映射。定义后,这些配置优先于上面的全局配置。
SOCIAL_AUTH_GOOGLE_OAUTH2_TEAM_MAP = {}
SOCIAL_AUTH_GITHUB_TEAM_MAP = {}
SOCIAL_AUTH_GITHUB_ORG_TEAM_MAP = {}
SOCIAL_AUTH_GITHUB_TEAM_TEAM_MAP = {}
SOCIAL_AUTH_SAML_TEAM_MAP = {}
取消注释以下行(即将 SOCIAL_AUTH_USER_FIELDS 设置为空列表),以防止创建新用户帐户。只有之前已经使用社交或企业级身份验证登录或用户帐户有匹配电子邮件地址的用户才能登录控制器。
SOCIAL_AUTH_USER_FIELDS = []
